Etch The Architecture
Etch Client Architecture
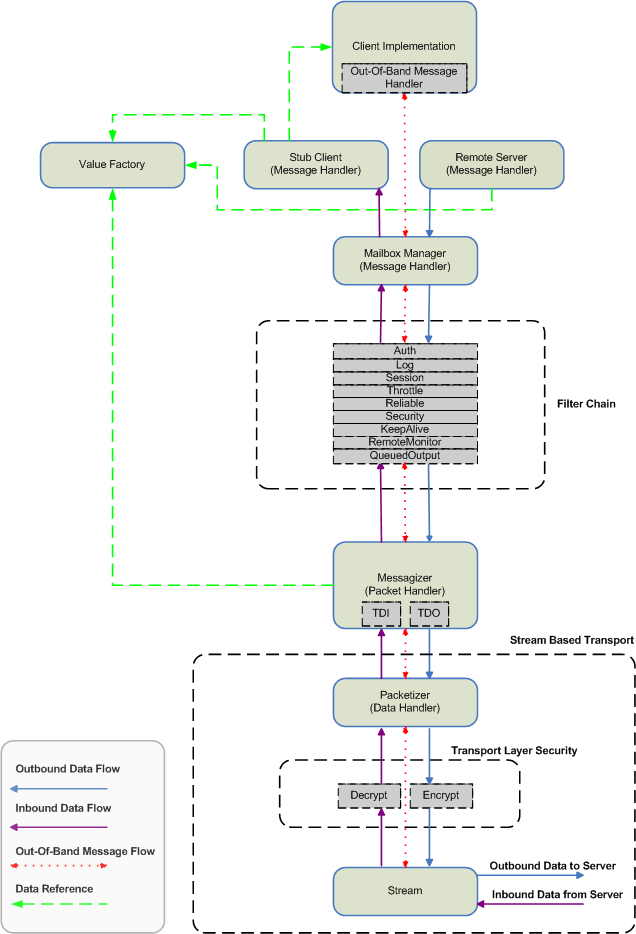
Etch Service Architecture

Datagram Based Transport
For datagram based protocol like UDP.

Core Modules
Listener
The listener for a transport accepts a connection and constructs a new server session to process messages on that connection for that session. In the case of TCP, the listener would normally be a TCP listening socket. For UDP, it might be an unconnected datagram socket
Value Factory
The value factory is the repository of the compiler generated service meta-data and methods for serializing and de-serializing custom data objects.
Out-Of-Band Message Handler
Normally the client or server implementation, the out-of-band message handler is the last handler in a chain which originates at the lowest level of the transport stack. Transport messages flow up the stack until someone handles them or they get to the top of the stack where the client or server implementation handles them. Transport messages are not the same as service messages, in that they communicate information about the transport stack itself.
Stub Client
The stub client accepts service messages not otherwise distributed to mailboxes by the mailbox manager, turning them into calls on the client implementation where they are handled.
Stub Server
The stub server accepts service messages not otherwise handled by the mailbox manager, turning them into calls on the server implementation where they are handled.
Remote Client
The remote client implements the client interface turning method calls into messages which are passed across the network to the stub client.
Remote Server
The remote server implements the server interface turning method calls into messages which are passed across the network to the stub server.
Mailbox Manager
When a call is made, the mailbox manager allocates a mailbox and ties it to the message id of the resulting message before it is sent. The mailbox manager then watches incoming messages, grabbing those that are responses and delivering them to their associated mailboxes.
Filter Chain
The filters get to watch, edit, or intercept service messages as they flow up and down the transport stack. Filters might also originate their own messages, originate or intercept out-of-band transport messages, and carry on a dialog with filters on the remote end of a session.
- Auth - the auth filter might add authentication data to outgoing messages and process authentication data on incoming messages when using a session based on a packet protocol; it might also dialog with an auth filter on the remote side to authenticate session based on a stream protocol.
- Log - records the incoming and outgoing messages.
- Session - when using a shared packet protocol, segregates the packets by session much like mailbox manager does.
- Throttle - limits the amount of traffic on a particular session.
- Reliable - adds reliability to an unreliable connection.
- Security - helper filter for Packet Layer Security. Assists with key changes.
- KeepAlive - periodic message to keep the connection open / detect connection failure.
- RemoteMonitor - records the incoming and outgoing messages to a remote service.
- QueuedOutput - used to queue outgoing packets for later delivery when it is important to not delay the sender.
Messagizer
The Messagizer intercepts messages flowing down the transport stack (say, from a filter or Mailbox Manager), reformats them into packets, and delivers them to a packet source for transport to the remote end of a session. Packets flowing up the transport stack are also reformatted into messages and delivered to a message handler (say, to a filter or Mailbox Manager). The message formatter is pluggable.
Packetizer
The Packetizer intercepts packets flowing down the transport stack (say, from Messagizer), reformats them into data, and delivers them to a data source for transport to the remote end of a session. Data flowing up the transport stack are also reformatted into packets and delivered to a packet handler (say, to Messagizer).
Transport Layer Security
Security encryption and message authentication which prevents snooping or tampering with the data stream.
Stream Protocol
A stream protocol such as TCP.
Optional Packet Oriented Protocol
If a packet oriented protocol is needed, the bottom three modules (Packetizer, Transport Layer Security, and Stream Protocol) are replaced with Packet Layer Security and Packet Protocol. These two modules serve an equivalent purpose. Care needs to be taken to manage the session, in particular session life cycle. |